Transposition Techniques
Blog post description.
Er. Shivam singh
9/19/20243 min read


Transposition Techniques in Cryptography: An Easy Guide
Transposition techniques are a fundamental part of cryptography, used to encode messages by rearranging the characters of the plaintext. Unlike substitution techniques, which replace characters, transposition techniques shuffle the order of the characters. This method helps to disguise the structure of the original message, making it harder for unauthorized parties to decipher. Let’s break down transposition techniques in a way that’s easy to understand.
What is Transposition?
Transposition in cryptography refers to the process of rearranging the characters of a message according to a specific system or pattern. The key idea is to keep the original characters intact but alter their positions to create ciphertext.
Basic Transposition Techniques
Here are some common transposition techniques:
Rail Fence Cipher:
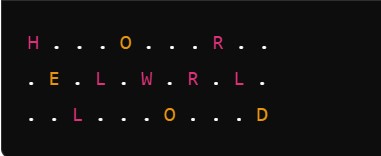
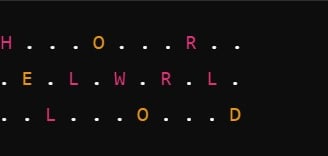
The Rail Fence Cipher is one of the simplest transposition techniques. It involves writing the plaintext in a zigzag pattern across multiple “rails” (rows) and then reading the ciphertext off row by row.
For example, let’s encrypt the plaintext “HELLO WORLD” using 3 rails:
Reading off each rail, we get the ciphertext: “HOR ELWL D”.
Columnar Transposition:
In Columnar Transposition, the plaintext is written out in a grid, and the columns are permuted according to a keyword. The ciphertext is then formed by reading the columns in the new order.
For example, if the keyword is “SECRET” and the plaintext is “MEET ME AT THE PARK”:
mathematica
Copy code
S E C R E T M E E T M E A T T H E P A R K
Number the columns according to the alphabetical order of the keyword: E, E, C, R, S, T. Read off the columns in the new order to get the ciphertext.
Transposition Cipher (Permutation Cipher):
This technique involves rearranging the characters of the plaintext based on a fixed permutation pattern.
For example, if the permutation pattern is (3, 1, 4, 2), it means the 1st character goes to position 3, the 2nd character goes to position 1, the 3rd character goes to position 4, and the 4th character goes to position 2.
For the plaintext “ABCD” and the pattern (3, 1, 4, 2), the ciphertext would be “CBAD”.
How Transposition Techniques Work
Here’s a simple overview of how transposition techniques are applied:
Create a Pattern or Key:
Decide on a pattern or key for rearranging characters. This could be a keyword, a numerical pattern, or a grid.
Write Out the Plaintext:
Depending on the technique, write the plaintext into a grid or arrange it according to the chosen pattern.
Rearrange Characters:
Apply the transposition pattern to rearrange the characters. This could involve moving characters between rows, columns, or positions according to the pattern.
Generate Ciphertext:
Read off the rearranged characters to form the ciphertext. The result will be a scrambled version of the original plaintext.
Decrypt the Ciphertext:
To decrypt, apply the reverse of the transposition pattern to recover the original plaintext from the ciphertext.
Advantages and Disadvantages
Advantages:
Maintains Character Integrity:
Unlike substitution ciphers, transposition techniques don’t alter the characters themselves, only their positions. This can make them simpler to implement and understand.
Adds Complexity:
Transposition adds an extra layer of complexity to the ciphertext, making it harder for an attacker to decode without knowing the pattern.
Flexible:
Various patterns and keys can be used, offering flexibility in how data is encrypted.
Disadvantages:
Vulnerability to Pattern Recognition:
Transposition techniques can be vulnerable to pattern recognition and frequency analysis, especially if the plaintext is long or has repeating patterns.
Not Enough Alone:
Transposition techniques are often not secure enough on their own. They are typically used in combination with substitution techniques for better security.
Complexity in Large Messages:
For very large messages, managing and applying transposition patterns can become complex and cumbersome.
Examples of Transposition Techniques in Use
Historical Examples:
Transposition ciphers have been used throughout history for military and diplomatic purposes. For instance, the Scytale cipher used by ancient Greeks involved wrapping a strip of parchment around a rod to encrypt a message.
Modern Use:
In modern cryptography, transposition techniques are often combined with substitution techniques to create more secure encryption methods. For example, the AES encryption algorithm uses multiple rounds of substitution and transposition to secure data.
© Copyright 2025 Skytpoint . All Rights Reserved.