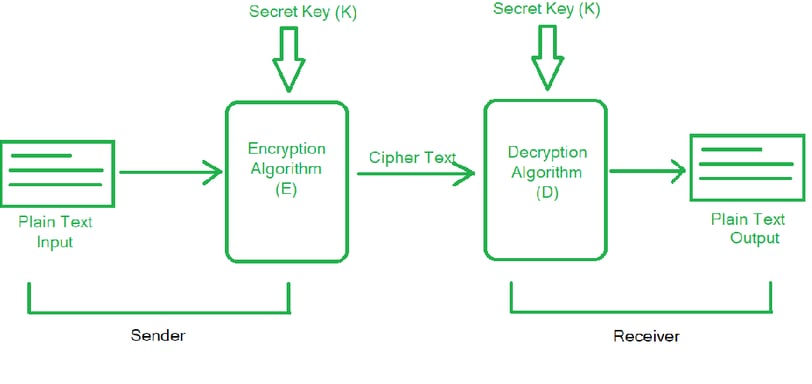
Symmetric Cipher Model
The symmetric cipher model is a fundamental and widely used approach to securing data. Its main strength lies in its speed and simplicity, making it suitable for a variety of applications. However, the challenge of key distribution and the risk of key compromise require careful management. Despite its limitations, symmetric encryption remains a vital part of modern cryptography, ensuring that our data stays safe from prying eyes in many of the technologies we use daily.
Er. Shivam Singh
9/19/20244 min read
Symmetric Cipher Model
The symmetric cipher model is one of the oldest and most widely used methods in cryptography to ensure data security. In simple terms, it’s a technique that uses the same key for both encryption (converting plaintext into ciphertext) and decryption (converting ciphertext back into plaintext). Let’s break it down step by step to understand how it works, its components, and why it’s so important.
Key Concepts of the Symmetric Cipher Model
Plaintext: This is the original message or data that you want to protect. For example, if you want to send a secret message like “Hello, Shivam,” that’s the plaintext.
Encryption Algorithm: The encryption algorithm is the method or process used to convert the plaintext into unreadable ciphertext. It applies mathematical operations and uses the secret key to scramble the data.
Ciphertext: Once the encryption algorithm is applied, the result is ciphertext—an unintelligible string of characters. For example, “Hello, Shivam” might become something like “Zxq92@lTs!”.
Secret Key: The secret key is a critical part of the symmetric cipher model. It is a piece of information (a sequence of bits) shared between the sender and receiver. Both parties must have the exact same key for encryption and decryption. If the key is lost or stolen, the security is compromised.
Decryption Algorithm: The decryption algorithm is used on the ciphertext to transform it back into the original plaintext. This process is essentially the reverse of encryption, and it also requires the secret key.
Key Sharing: In the symmetric cipher model, one of the biggest challenges is securely sharing the key between the sender and receiver. If the key falls into the wrong hands, the data can be decrypted and understood by unauthorized people.
How Does the Symmetric Cipher Model Work?
To understand this model in action, let’s walk through an example:
Step 1: Sender Encrypts the Message:
Suppose you want to send a secret message: “Transfer ₹5000”.
You use an encryption algorithm (such as the popular AES, DES, or RC4) and a secret key (for example, “A1B2C3D4E5”).
The encryption algorithm scrambles the message using this key, turning it into unreadable ciphertext: “9Xf12P@Kx$”.
Step 2: Sender Sends the Ciphertext:
After encrypting the message, the sender transmits the ciphertext (“9Xf12P@Kx$”) over the network. Anyone intercepting this message will see only the scrambled characters, which are meaningless without the key.
Step 3: Receiver Decrypts the Ciphertext:
The receiver, who has the same secret key (“A1B2C3D4E5”), uses the decryption algorithm to convert the ciphertext back into the original message.
The decryption algorithm takes the ciphertext “9Xf12P@Kx$” and the secret key, and it outputs the original message: “Transfer ₹5000”.
This simple process shows how the symmetric cipher model provides confidentiality, ensuring that only authorized users who have the secret key can read the data.
Types of Symmetric Ciphers
There are two main types of symmetric ciphers:
Stream Cipher:
Stream ciphers encrypt data one bit or byte at a time.
They are fast and often used for real-time communication, such as voice calls or video streaming.
Example: RC4 (Rivest Cipher 4).
Block Cipher:
Block ciphers encrypt data in fixed-size blocks, typically 64 bits or 128 bits at a time.
They are widely used for securing data at rest, such as files or databases.
Examples: DES (Data Encryption Standard), AES (Advanced Encryption Standard), 3DES (Triple DES).
Advantages of Symmetric Ciphers
Fast and Efficient:
Symmetric ciphers are faster and more efficient compared to other encryption techniques (such as asymmetric encryption). This makes them ideal for encrypting large amounts of data, like files, databases, or streaming media.
Easy to Implement:
Symmetric algorithms are relatively straightforward to implement and require fewer computational resources, making them suitable for devices with limited processing power (like smartphones or IoT devices).
Widely Used:
Symmetric encryption is used in many everyday applications, such as SSL/TLS for secure web browsing, file encryption tools (like WinZip or 7-Zip), and wireless communication protocols (like WPA2 for Wi-Fi).
Challenges of Symmetric Ciphers
Key Distribution:
One of the biggest challenges with symmetric encryption is securely distributing the key to both the sender and receiver. If the key is exposed during this process, the entire system is compromised.
In large networks or systems with many users, managing and distributing keys can be difficult.
Lack of Scalability:
In scenarios where many people need to communicate securely, symmetric encryption becomes inefficient. Every pair of users needs a unique key, leading to a large number of keys to manage.
For example, if 10 people need to communicate with each other securely, they will need 45 unique keys (one for each pair of users).
Security Risk if Key is Stolen:
If the secret key is stolen or compromised, the attacker can decrypt all communications encrypted with that key. This is a significant risk because both encryption and decryption use the same key.
Popular Symmetric Encryption Algorithms
AES (Advanced Encryption Standard):
AES is the most widely used symmetric encryption algorithm today. It is fast, secure, and supports key sizes of 128, 192, or 256 bits.
It is used in a wide range of applications, from securing sensitive data on government systems to protecting your Wi-Fi connection.
DES (Data Encryption Standard):
DES was one of the earliest symmetric encryption standards. It uses a 56-bit key to encrypt data in 64-bit blocks.
However, DES is now considered insecure because its key size is too small, making it vulnerable to brute-force attacks.
3DES (Triple DES):
3DES was developed as an enhancement of DES by applying the DES algorithm three times to each data block. This increased security but also made it slower.
3DES is still used in some legacy systems but is being replaced by AES due to performance and security improvements.
© Copyright 2025 Skytpoint . All Rights Reserved.